Over the past few years, a number of internet Service Providers (ISPs) have upgraded to 100 Gigabit core networks. Many have found success using Mikrotik on the path to 100Gb core using Layer 2 VPN technology like VPLS. With the proper hardware and design, this...
Network Operating System
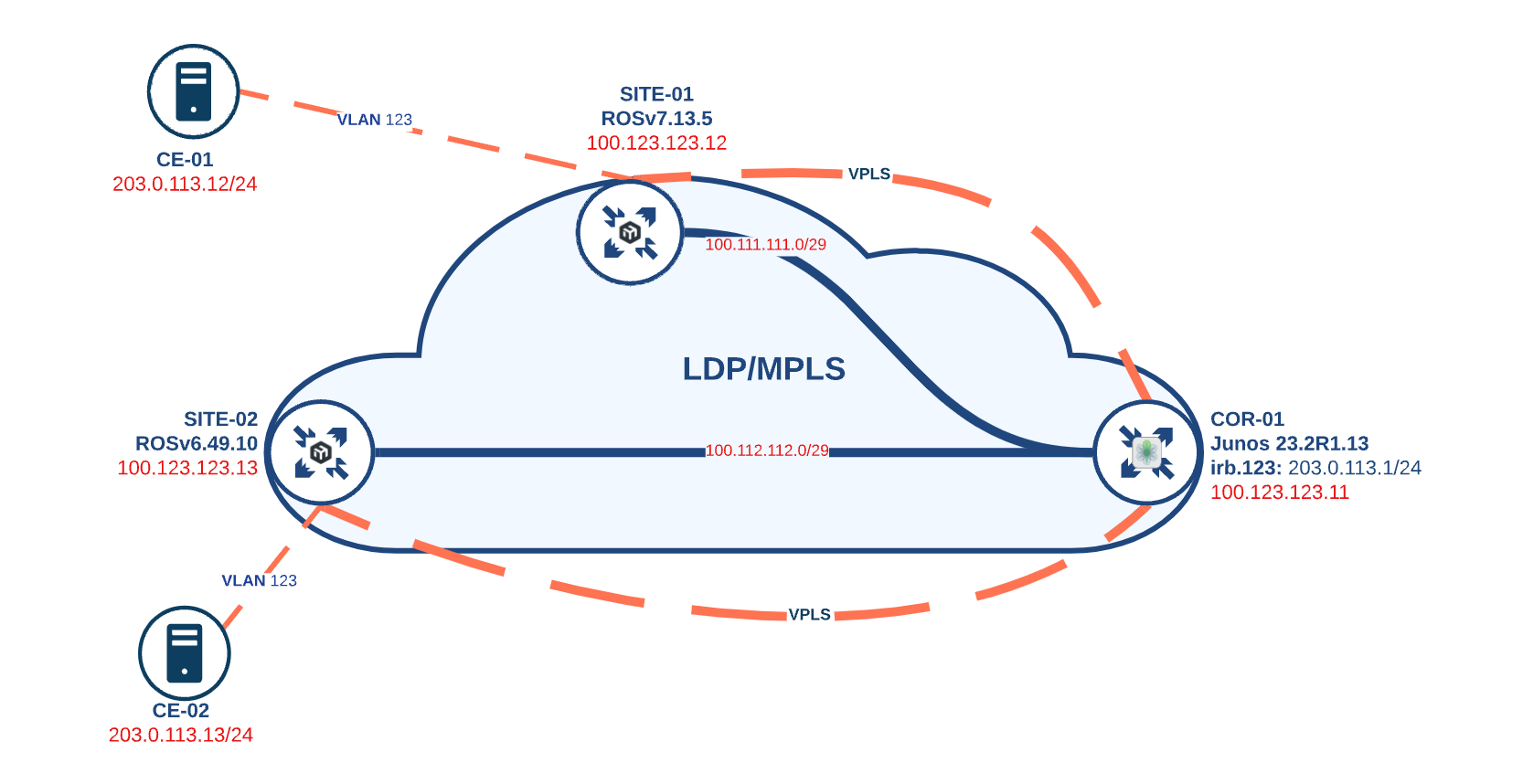
JunOS and RouterOS LDP InterOP
Virtual Private LAN Service (VPLS) is one of the most widely used components to extend layer 2 domains for disparate locations in Service Provider environments. VPLS creates an emulated 'Pseudo-LAN' by combining Layer 2 ethernet and Label Switched Paths. In network...

MikroTik CCR 1009/1016/1036 officially discontinued
We knew it was coming when MikroTik announced the end of production for Tilera chips back in the fall of 2022, but recently (looks like it was last week), MikroTik moved almost all of the CCR1K series (CCR1009, CCR1016, CCR1036) to discontinued officially on the...

MikroTik RouterOS v7.11 stable released
2023 has been a big year for MikroTik RouterOS v7 development. The OS has matured quite a bit and the number of operators that are using ROSv7 in prod has gone up significantly. Most of the work this year has been centered around...

MikroTik introduces Back to Home (bth) VPN in ROS 7.11 beta/rc
Back To Home - RouterOS - MikroTik DocumentationMikroTik already has a wealth of VPN options and is introducing another with the Back to Home or BTH VPN service. The framework underneath is based on wireguard which MikroTik began supporting in the early 7.x series of...

MikroTik RouterOS v7.5 stable released
The pace of development for MikroTik RouterOS version 7 has definitely sped up in 2022 and we are seeing the results in improved stability and features added. As of August 31st, 2022, MikroTik moved ROS v7.5rc2 into v7.5 stable MikroTik Routers and Wireless - Software...

Networking CLI Rosetta Stone
Changing between network operating systems is one of the most challenging things for new engineers. Most people learned cisco cli due to their extensive training system or got on the job training for whatever their company runs. We are hoping to make moving back and...
 +1 (855) 645-7684
+1 (855) 645-7684